SUMMARY
The following instructions outline connecting Single Sign-On for your site via Microsoft Azure Active Directory (Azure AD).
CONTENT
Single Sign-On (SSO)
SSO is an optional PowerDMS feature that allows our customers to simplify their authorization process when signing into their computer and its programs. SSO uses the customer's domain credentials, management system, and login pages, so only one sign-in is necessary for users to access their organization's site and PowerDMS.
For SSO to work for all users within your site, Site Administrators must turn SSO on from their Administration Menu > Settings > Security > Single Sign On.
Only one SSO connection is allowed per site.
Contact your PowerDMS CSM for your SSO Application licensing information.
| Note: To use OIDC/OAuth, the application requires access to user information. This permission will carry forward to new users and groups as well. |
Configuring SSO for Azure AD
You can leverage Azure AD for SSO in PowerDMS through OpenID Connect (OIDC).
-
First, you'll create an App Registration in your Azure instance. PowerDMS will need the following from you:
-
Your tenant domain and any domain aliases you're using.
-
An application (client) ID from the app registration you build.
-
A client secret value from the app registration you build.
- Navigate to Azure Active Directory > App Registrations and click New Registration.
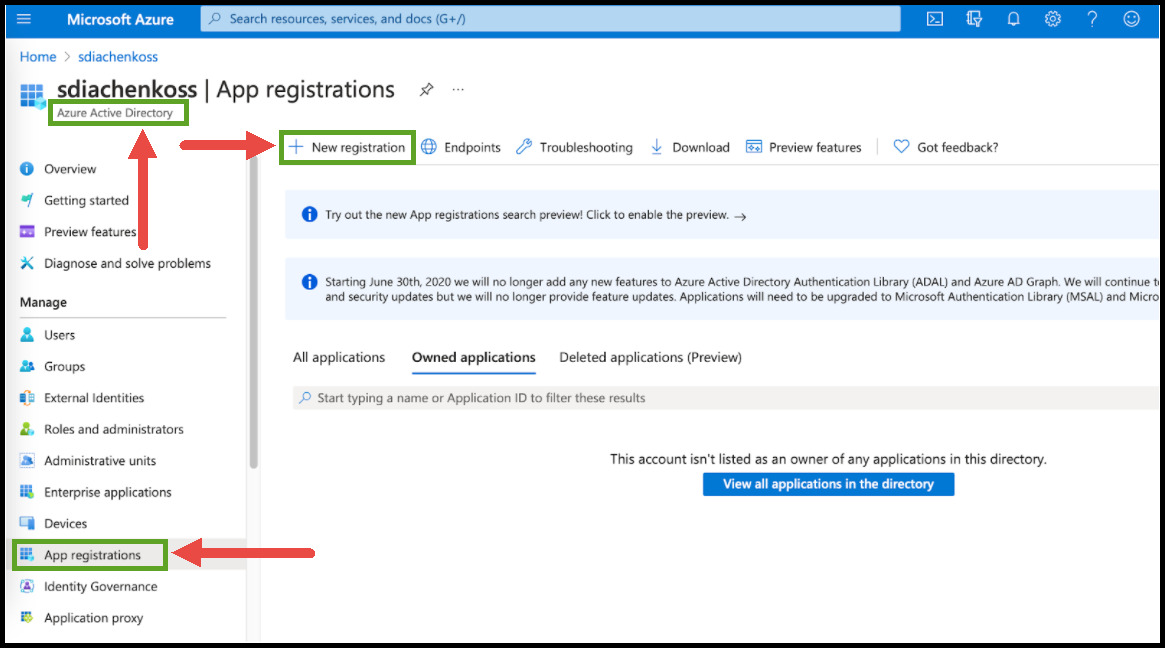
-
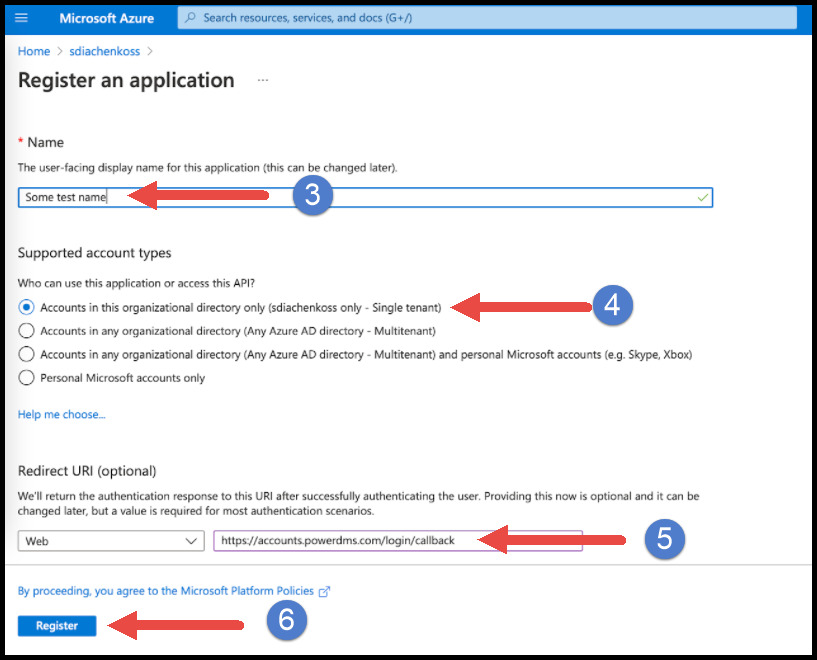
Provide an easily identifiable name on the screen that comes up.
-
Click the circle next to Accounts in this organization directory only.
-
Select Web from the drop-down menu and paste the following into the Redirect URI section: https://accounts.powerdms.com/login/callback.
-
Click the Register button.
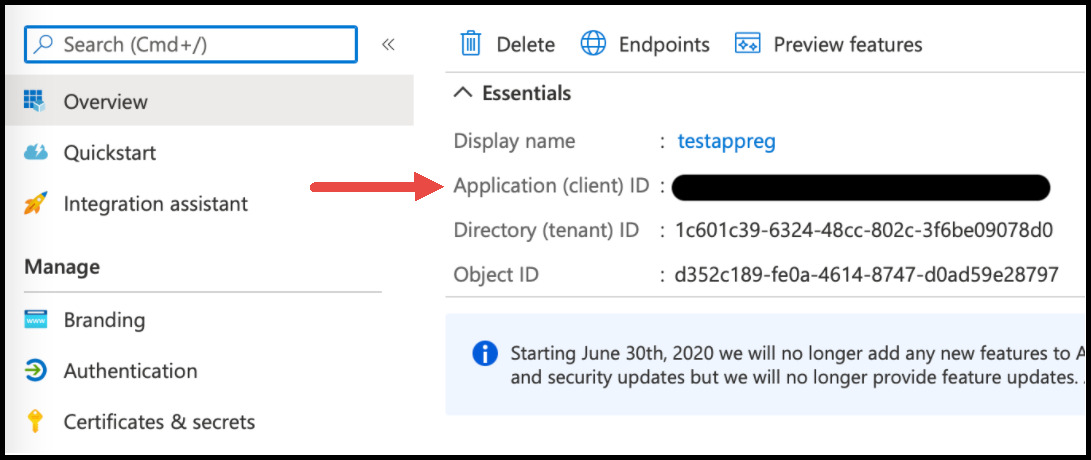
-
On the next page, copy the Application (client) ID value. You will need to provide this to PowerDMS.
-
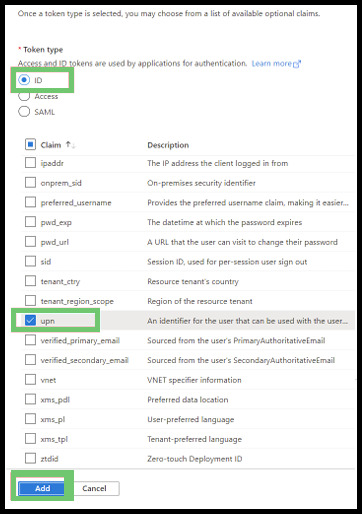
From the left-hand sidebar menu, select Token Configuration and then click Add Optional Claim.
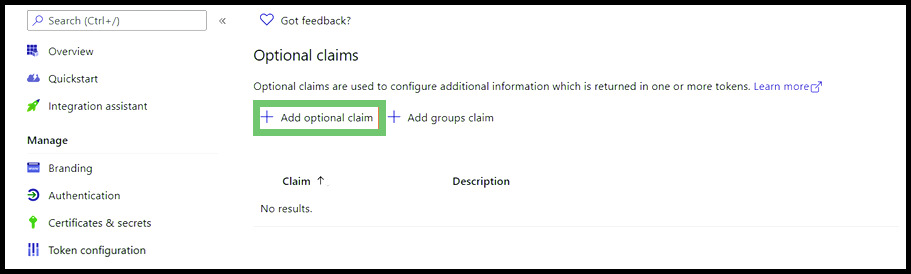
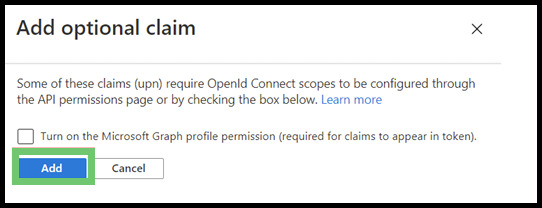
- Select the ID radio button, then check the box next to UPN. Click the Add button at the bottom of the prompt, then click Add again on the page that pops up.
Note: Your usernames in UPN must match those in PowerDMS before using this feature. If usernames don’t match, your users will experience an error, will not be able to log in (unless they use the SSO bypass link and know their PowerDMS Forms password), and could potentially lock themselves and their whole agency out of the site.
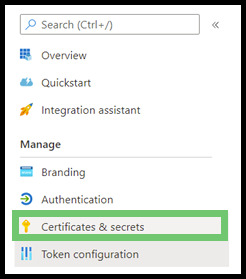
- In the left-hand sidebar menu, select Certificates and Secrets.
-
On the page that appears, click New client secret.
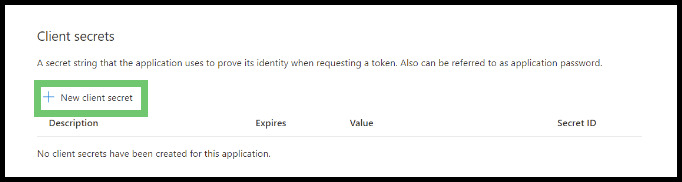
- On the popup, provide an easily identifiable Description (such as "accounts.powerdms.com") and select an expiration for the Client Secret. Click the Add button.
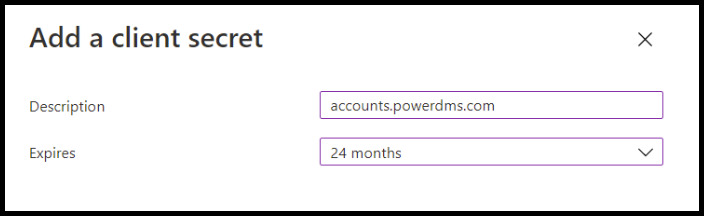
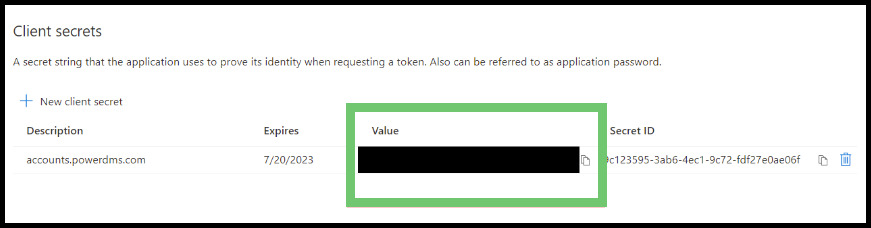
- Copy the string from the Value column and set it aside for later use.
-
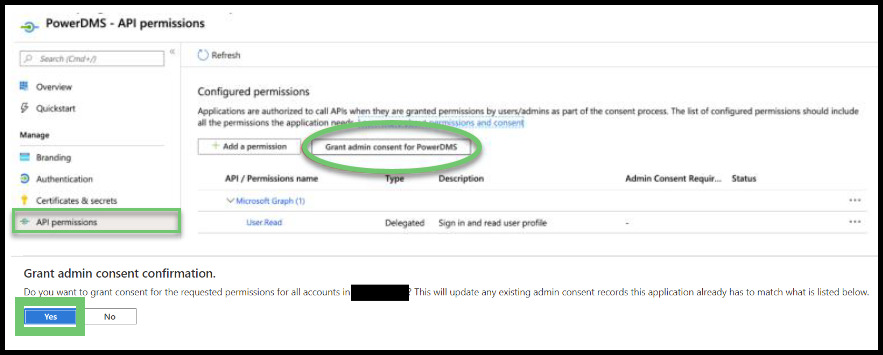
Click API Permissions in your left-hand sidebar menu. On the page that appears, click the Grant admin consent button and the Yes button in the screen's bottom left corner.
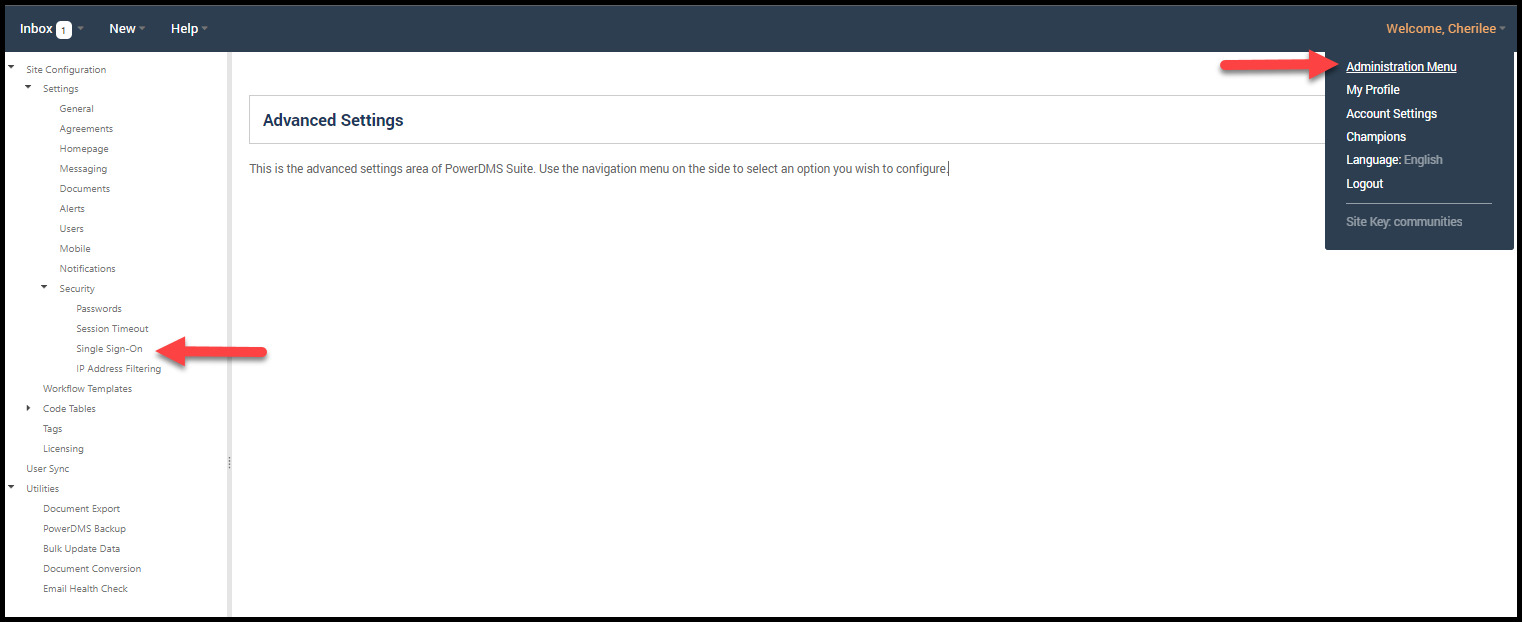
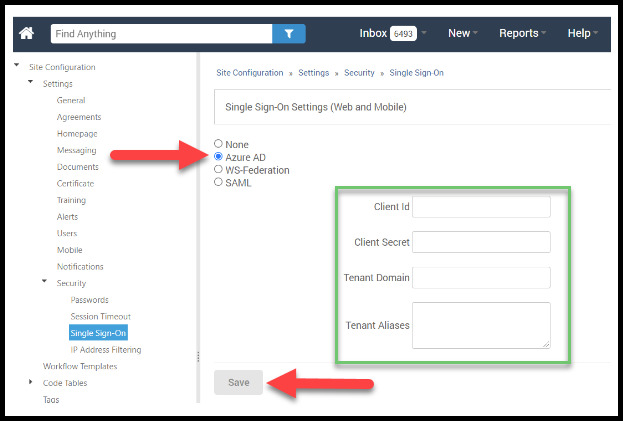
- Log into your PowerDMS site and open the Administration Menu from the drop-down menu below your name in the upper right corner of your screen. Navigate to Settings > Security > Single Sign On.
-
Select the Azure AD radio button.
-
Paste in your copied Application (client) ID, Client Secret Value, and Tenant Domain. You may also want to enter any domain aliases your organization may use, with each one separated by a comma, but this is optional.
-
Click Save.
-
To test your SSO, try to log into PowerDMS as a synced user. You should automatically be redirected to your corporate login page.
Note: To test with Pilot Users:
- Log into your PowerDMS site using Azure AD SSO.
- Assign users to the Azure AD app and check they were provisioned into PowerDMS.
Having Sign-In Issues?
If your SSO isn't working, you can still log into your PowerDMS site using your Admin username and password. Go to https://powerdms.com/ui/login.aspx?formsauth=true.
If SSO login errors persist, please contact PowerDMS Support.
The System for Cross-domain Identity Management (SCIM) protocol follows all error codes and messages. Please, save any error messages by taking screenshots or copying the message's details. PowerDMS may need these to help you.
RELATED ARTICLES
Article: Configuring Microsoft ADFS 2.0 for PowerDMS Federation
Article: Configuring SAML for PowerDMS
Article: PowerDMS Basic User Guide
Article: PowerDMS Mobile SSO Single Sign On
Article: PowerDMS Site Preparation
SECURITY REQUIRED
Site Administrator
